Видео с ютуба Cache Attack

RuhrSec 2016: "Cache Side-Channel Attacks and the case of Rowhammer", Daniel Gruss

USENIX Security '19 - ScatterCache: Thwarting Cache Attacks via Cache Set Randomization

DNS Cache Poisoning - Computerphile

Demo: Cache Template Attack on Keystrokes
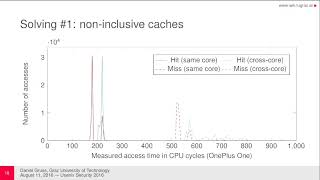
USENIX Security '16 - ARMageddon: Cache Attacks on Mobile Devices

ZDM#1 - Cache timing attacks: How do they work?

USENIX Security '22 - Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses

Page Cache Attacks: Microarchitectural Attacks on Flawless Hardware

Cache Attack Types and Mitigations #2 - Thorn Tech

Cache-timing attacks on AES

Last-Level Cache Side-Channel Attacks are Practical

USENIX Security '17 - AutoLock: Why Cache Attacks on ARM Are Harder Than You Think

Scatter and Split Securely: Defeating Cache Contention and Occupancy Attacks

Flush based Cache Side Channel Attacks and Defense

Cache-Timing Attacks on RSA Key Generation

How to Stop Cache Attacks Like Flush+Reload, Flush+Flush and Prime+Probe?

Your Cache is My Cache: Detecting Cache Based Side Channel Attacks with ML and Performance Counters

USENIX Security '15 - Cache Template Attacks: Automating Attacks on Inclusive Last-Level Caches

USENIX Security '21 - MIRAGE: Mitigating Conflict-Based Cache Attacks with a Practical...

USENIX Security '18 - Malicious Management Unit: Why Stopping Cache Attacks in Software...